Vince Kuchar, CEO of RMC Global, & Trae Mazza, Senior Security Engineer
At the heart of smart city innovation lies Advanced Metering Infrastructure (AMI), a pivotal technology reshaping energy management and consumption.
Smart cities, by definition, harness information and communication technologies to enhance operational efficiency, thereby elevating the quality of municipal services and residents’ lives. Integral to these urban ecosystems are sensors and embedded devices spanning across various domains – from utility management and electric vehicle charging, to public safety tools that detect specific noises such as gunfire and shattering glass. These technologies, interconnected through wireless networks designed to scale with thousands and even millions of devices, comprise the foundation of a smart city’s operational framework.
Much like the Operational Technology (OT) systems that underpin many industrial processes, AMI is an integrated system of smart meters, communication networks, and data management systems that enables the bidirectional flow of information between utilities and consumers. This technology allows for the real-time monitoring and management of energy consumption, enabling accurate billing and the efficient distribution and use of electricity. Yet, the expansive network of meters, gateways, and management infrastructure that helps AMI achieve energy efficiency comes at a cost: an expanded attack surface for potential cyber threats.
These systems, crucial for the seamless operation of the electrical grid, can be targeted to disrupt services, manipulate data, or gain unauthorized access. Since these systems are often scattered throughout cities in unmonitored public areas, the physical accessibility of these devices amplifies the risk for sophisticated malware attacks on centralized data hubs and remote management functions.
In this regard, AMI represents a dichotomy of innovation and vulnerability. Drawing from RMC’s extensive experience in penetration testing and security assessments, we’ve observed that attackers in the AMI sphere often exploit inherent vulnerabilities, mirroring the challenges faced in securing OT environments. The accessibility of AMI components, coupled with their reliance on potentially outdated technologies, present unique challenges that require a nuanced, strategic approach to security.
A strategic blueprint for effective AMI security involves a deep understanding of the system architecture, from field-deployed devices to back-end applications, and a keen focus on the operational context. This approach prioritizes not just the technical vulnerabilities but their impact on critical operations, ensuring that security measures align with the operational imperatives of utilities and smart cities at large.
Proactive cybersecurity measures, including robust protocols, regular security assessments, and strategic partnerships with cybersecurity experts, are essential to safeguarding AMI systems and urban energy. As we navigate through this complex modern landscape, the commitment to securing the foundational elements of our smart cities has never been more critical.
Exploring Wireless Technologies in Smart Cities
To ensure these myriad devices can communicate effectively across large areas, smart cities employ several wireless technologies. While there are numerous factors to consider when selecting a technology—ranging from cost to device support—our focus is on security.
Three key wireless technologies stand out in the smart city landscape:
- Wi-SUN (Wireless Smart Utility Network): Notable for its robust security features, Wi-SUN incorporates IEEE 802.11i Key Management for coordinating key usage across the network and IEEE 802.1X authentication for secure credential verification, ensuring certificate-based mutual authentication between devices and the network.
- LoRaWAN (Long Range Wide Area Network): Known for its long-range capabilities, making it suitable for widespread urban applications.
- NB-IoT (NarrowBand-Internet of Things): Focused on providing reliable communication over a narrow bandwidth; ideal for simple, low-power devices.
Among these, Wi-SUN stands out as particularly security-focused, making it a preferred choice for smart city deployments seeking to safeguarding their infrastructure.
Securing the Architecture of a Wi-SUN Smart City Deployment
A Wi-SUN smart city deployment is structured to ensure reliability and security at every layer. At the foundational level, there are various endpoint devices or sensors, termed as nodes within the Wi-SUN network. These nodes, which include everything from utility meters to traffic management devices, form a resilient mesh network. This redundancy means that even if some sensors fail, the network self-heals, maintaining uninterrupted communication.
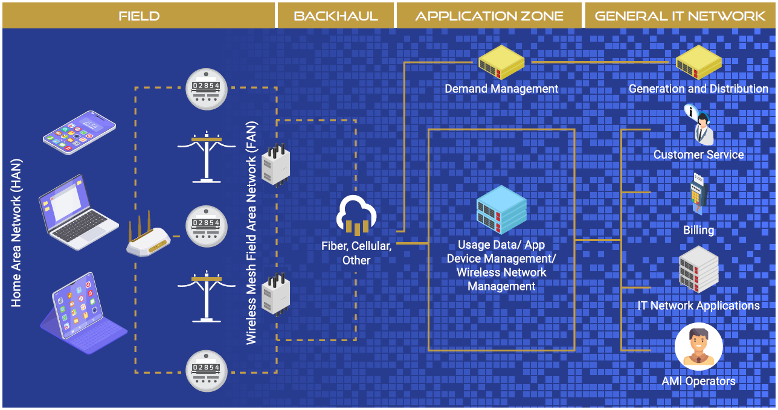
Border routers serve as the critical bridge between the local Field Area Network (FAN) and the broader Wide Area Network (WAN). Positioned in relatively secure locations like light poles or within utility substations, these routers manage their respective segments of the smart city, ensuring that nodes are appropriately configured to communicate within the FAN.
The connectivity between border routers and the operator’s backend systems is typically maintained through cellular or fiber transmission links, culminating in the Network Operations Center (NOC). The NOC represents the central hub for managing the Wi-SUN FAN deployment and its devices, whether it’s hosted on-premises, in the cloud, or a hybrid setup.
The critical role border routers play in Wi-SUN smart cities also marks them as prime targets for cyber attacks. Despite Wi-SUN’s robust security, our assessments reveal that attackers can bypass it by exploiting border router vulnerabilities, from easy-to-guess passwords to outdated firmware. Breaches in AMI systems can have dire consequences, such as attackers gaining extensive access to manipulate field devices, potentially causing widespread power outages or interfering with critical communication services. Furthermore, infiltrating the utility’s backend networks could compromise other essential systems, leading to cascading failures impacting not just energy distribution but also emergency response systems, public safety, and the economic stability of the region.
To counteract these threats, a comprehensive approach involving network segmentation, stringent access controls, and regular penetration testing is recommended. Recurring updates, monitoring, and the implementation of robust encryption protocols are also crucial in defending against both physical and cyber threats. By enhancing the security posture of border routers and the wider AMI network, utilities can safeguard against unauthorized access, ensuring the reliability and efficiency of smart city infrastructures.
Fortifying the Future: RMC’s Vision for AMI Security
When it comes to AMI security, experience matters. RMC is dedicated to enhancing AMI security in smart cities by leveraging our extensive OT cybersecurity expertise. Our approach includes comprehensive penetration testing across AMI systems, assessing vulnerabilities from physical and cyber threats to prevent potential disruptions and ensure the integrity of the power grid. By focusing on hardening devices against attacks, encrypting communications across all networks, and rigorously testing backend applications for vulnerabilities, we aim to mitigate risks and enable utilities to maximize the benefits of AMI systems, ensuring a secure and efficient future for smart infrastructure.
How can RMC help your organization?
Contact us today: sales@rmcglobal.com
Be sure to follow RMC Global on LinkedIn, and bookmark our News & Perspectives website to stay apprised of industry insights and topical advice on establishing cyber resiliency in OT environments.


